41 advanced antivirus techniques in network security
Advanced Endpoint Protection Protects You From Dated ... Advanced Endpoint Protection Protects You From Dated Antivirus. Despite attempts to pivot from outdated security methodologies, traditional antivirus (AV) continues to fail to prevent security breaches on endpoints, as evidenced by the rise in security breaches worldwide. Moreover, AV requires layers of products, saddling organizations with ... Combating Advanced Evasion Techniques with Network ... Testing the effectiveness of Network Security Platform against advanced evasion techniques You can use an advanced evasion technique testing tool to test the effectiveness of McAfee Network Security Platform against advanced evasion techniques. For this article, we show this test using McAfee (Stonesoft) Evader.
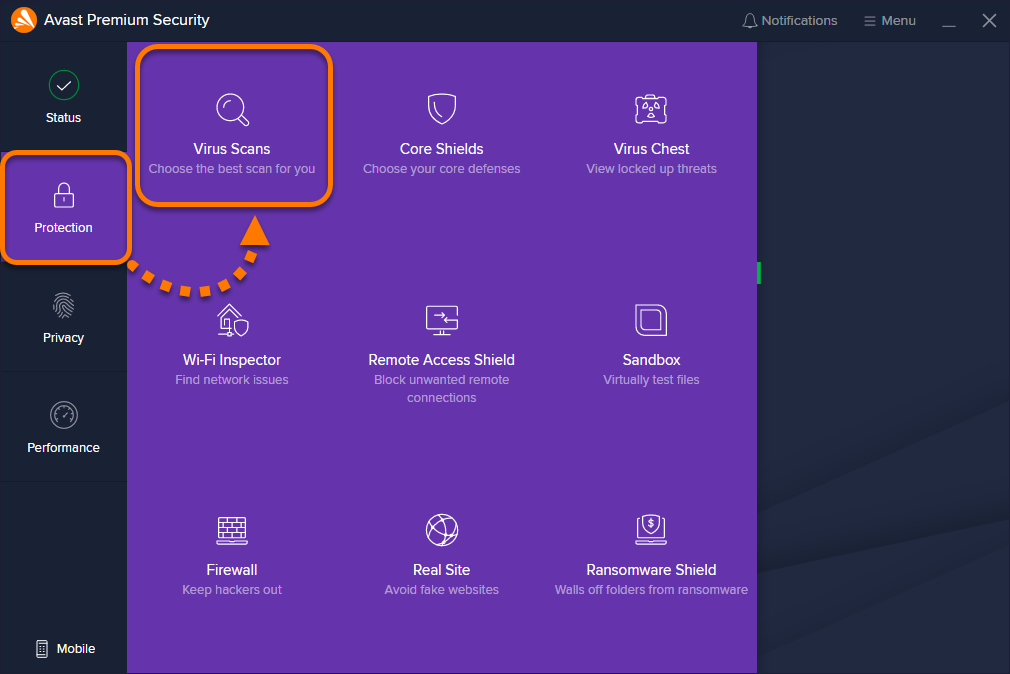
Internet Security with antivirus protection | ESET Get advanced protection with award-winning antivirus for your everyday online activities, ... rootkits, worms and spyware. Also protects against techniques that seek to evade detection, and blocks targeted attacks and exploits. Explore all features in detail. Try before you buy - …

Advanced antivirus techniques in network security
PDF IT-2710: Advanced Topics in Network Security Provides in-depth understanding of network security principles and the tools and configurations needed to secure a network. Credit Hour(s): 3 Lecture Hour(s): 2 Lab Hour(s): 2 Requisites Prerequisite and Corequisite ITNT-2370 Network Security Fundamentals. Outcomes Course Outcome(s): Apply knowledge of advanced network security principles to ... Network Antivirus: Sophos Advanced Security with EDR, MDR The world's best network antivirus solution Sophos antivirus protection for networks is built to stop ransomware, viruses, and advanced malware attacks in their tracks. Combining the industry's leading malware detection with endpoint detection and response (EDR), Sophos will future-proof your organization against both new and old threats. Malware Prevention: A Multi-Layered Approach - Cynet NGAV can detect and prevent malware that does not match a known binary signature, as well as fileless attacks that execute in memory or via network protocols without downloading a file to the target device. Control Privileges Control privileges on endpoints, servers, even administrator accounts, using the least privilege principle.
Advanced antivirus techniques in network security. Worry-Free Services Advanced: Cloud-Based ... - Trend Micro A blend of cross-generational threat techniques gives you the broadest protection against advanced threats. Take advantage of: High-fidelity machine learning, which uniquely analyzes files - not only before execution, but also during runtime More reliable detection of advanced malware, including fileless, cryptomining, ransomware, and more PDF . Etworkand3ecurity2esearch#Enter $Epartmentof# ... CSE545 - Advanced Network Security - Professor McDaniel Page Why are we here? -- Goals • Our goal: to provide you with the tools to perform research in . ‣ Evaluating network security techniques ‣ Designing network security solutions ‣ Attacking network infrastructure ‣ Developing analysis methods • This is going to be a time-consuming course. The key 10 Malware Detection Techniques Used by AntiVirus. How ... An AntiMalware, also known as AntiVirus, uses multiple technologies, algorithms, and analysis techniques for detecting viruses and all of the other types of malware.All of this is happening in real-time in the background of your computer. Here are the 10 Malware Detection Techniques used by Antivirus/Antimalware software to detect Viruses, Worms, Adware, Spyware, Ransomware, Trojan Horse, and ... Malware Delivery Campaign Employs Advanced Fileless Techniques "Both the distributed network infrastructure and the advanced fileless techniques allowed this campaign fly under the radar for a while, highlighting how having the right defensive technologies is of utmost importance in order to detect and counter these attacks in a timely manner," Microsoft concludes.
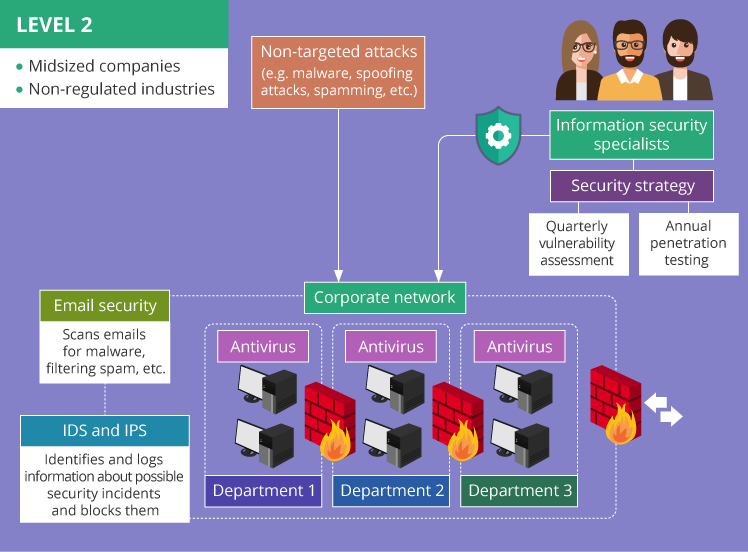
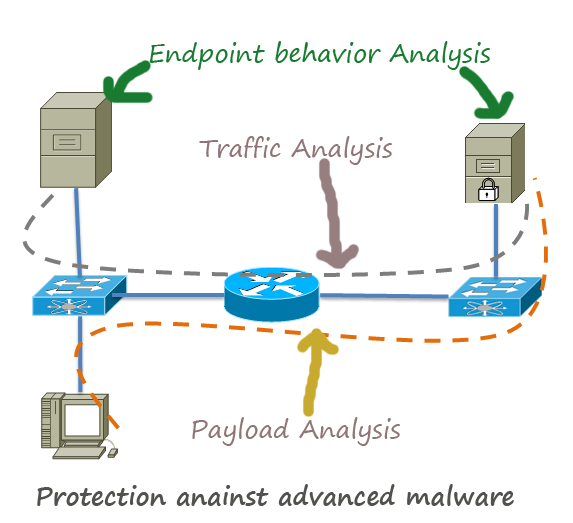
What Is Advanced Malware Protection? - Cisco Traditional antivirus solutions may struggle to accurately detect low-prevalence threats. But endpoint security that employs continuous monitoring of all file activity results in faster detection of new threats. New antivirus capabilities were developed to detect and mitigate zero-day attacks and other, more sophisticated malware. How to Protect Networks against Advanced Evasion ... Evasion techniques evade the exiting network security devices such as signature based IPS and firewalls to enter the internal network to deliver exploits in servers. Most of the Intrusion detection and prevention system rely on attack signatures to identify malicious strings in the traffic. Breach Detection | How to Choose Comodo Advanced Threat ... Breach detection systems (BDS) refer to a category of advanced threat protection solutions that consists of applications and security devices. These security tools are made to detect any forms of malware inside a network after an incident of a breach has occurred. This type of advanced threat protection solution is a powerful tool against a ... What is Advanced threat protection? | VMware Glossary Advanced Threat Protection (ATP) is a suite of analysis tools designed to defend against advanced threats that use known and unknown attack vectors.ATP augments more common security solutions aimed at repelling known intrusion strategies. Advanced threats are those that seek to surreptitiously gain access to a network and remain, undetected, in that network for months or even years ...
Advanced Executive Program in Cybersecurity | Edureka ... Advanced Executive Program in Cybersecurity by Edureka is top course for Cloud & Security. ... Asymmetric Key Cryptography Attack Prevention Techniques Cloud Security 101 Credential Analysis Hacking Tools Cryptography Techniques Network Security SQL Injection Web Application Security Ethical Hacking. ... System Security and Protection 4. Basics ... Workshop on "Blockchain Technology and Advanced ... The proposed network model will support high-speed transmission. So, the outcome of the proposal will be much useful where high internet traffic exists. Additionally, the proposed technology considering and providing protection on all types of security concerns by designing the required security protocol of the proposed network. Advanced Information Security Essentials Course ... SEC501: Advanced Security Essentials - Enterprise Defender is an essential course for members of security teams of all sizes. That includes smaller teams where you wear several (or all) hats and need a robust understanding of many facets of cybersecurity, and larger teams where your role is more focused, and gaining skills in additional areas ... 11 Best Network Security Software Reviewed | 2022 They use a combination of different techniques to defend your system, and they scored a perfect 100% in independent testing when it came to protection. ... Vipre Advanced Security offers some great features. They have all of the things you would expect in an antivirus and network security suite but offer it at a lower price than a lot of their ...
Advanced Network Security (CS4155) - Cyber Threat Intelligence Advanced Network Security (CS4155) About this course ET4397IN provides a general overview of network security, attacks and countermeasures. In Advanced Network Security, we will go a lot deeper and take a more technical approach to communication security.
Anti-Malware Advanced Threat Protection & Removal | Trend ... Non-signature based detection methods are designed to detect these kinds of attacks. These XGen™ security techniques include, but are not limited to, custom sandboxing, behavioral analysis, intrusion and exploit prevention, investigation and forensics, memory inspection, prevalence/maturity checks, and application control.
What Is an Advanced Persistent Threat (APT)? As the name "advanced" suggests, an advanced persistent threat (APT) uses continuous, clandestine, and sophisticated hacking techniques to gain access to a system and remain inside for a prolonged period of time, with potentially destructive consequences. The Prime Targets of Advanced Persistent Threats
What Is Network Security | Network Security Solutions | EC ... The safety of data is only made possible by implementing useful network security tools and techniques. The importance of network security in the modern business atmosphere has increased after a major portion of the workforce went remote due to COVID-19. Today, the office system is distributed in one huge network across multiple locations.
Sophos Endpoint Protection: Intercept X with EDR, XDR Intercept X Advanced with XDR is the industry’s only XDR solution that synchronizes native endpoint, server, firewall, email, cloud and O365 security. Get a holistic view of your organization’s environment with the richest data set and deep analysis for threat detection, investigation and response for both dedicated SOC teams and IT admins.
Spam, Malware, and Advanced Threat Protection | Barracuda ... Advanced Premium Premium Plus + Spam and Malware Protection Identify and block spam, viruses, and malware delivered via email messages. Using virus scanning, spam scoring, real-time intent analysis, URL link protection, reputation checks, and other techniques, Barracuda scans email messages and files. + Attachment Protection
Advanced Threat and Network Analysis: Your Security Secret ... As criminals develop increasingly sophisticated attack modes, having effective endpoint protection is just one element of the security equation. Today, blocking the latest exploits requires a combination of advanced threat and network protection techniques that help you predict and influence outcomes, not merely react.
Foundational Security VS Advanced Cybersecurity-Corsica ... Advanced Security controls include: Managed Detection and Response (MDR) —Most organizations do not possess the resources they need in order to investigate and proactively hunt for abnormal behavior. They lack the ability to see beyond suspicious activity.
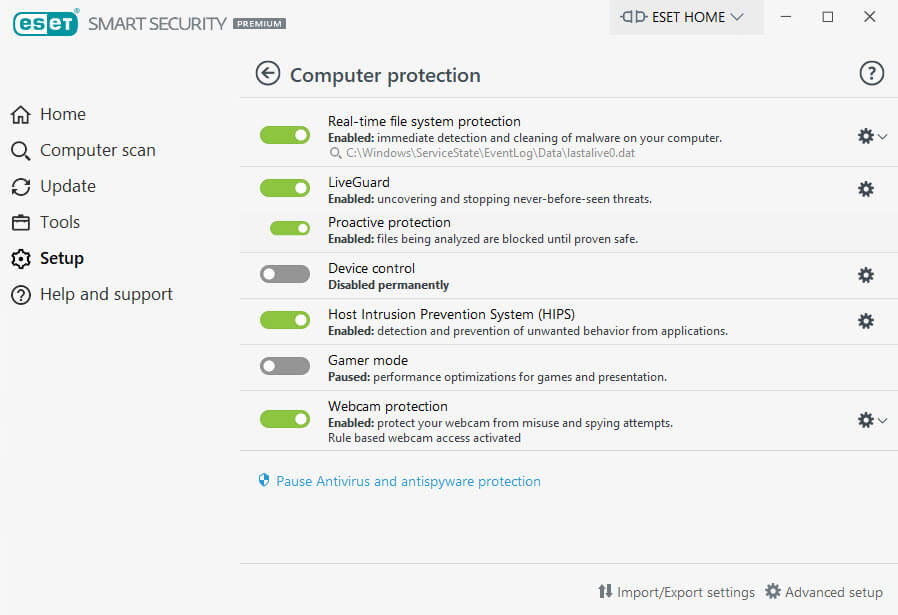
ESET Endpoint Protection Advanced: Quick Solution Overview ESET Endpoint Antivirus helps protect against some network attacks by monitoring network traffic and blocking any traffic deemed as harmful. The Management Console ESET Cloud Administrator is a cloud-based management tool that enables you to manage security using a single console. Here is what you need to know about the management console:
Cybersecurity Techniques: Reactive vs. Proactive ... Endpoint protection helps an enterprise avoid losing control over sensitive data when it's copied to an external device or when network access is gained through an unsecured endpoint. Endpoint protection is one of the key elements of modern business security. Should your company choose proactive or reactive cybersecurity techniques?
PDF Section 4 - Network Security & Advanced Device Techniques NETWORK SECURITY & ADVANCED DEVICE TECHNIQUES Chris Dawe & Tom Bridge. NONE OF THIS SHOULD WORK. ... WIRED EQUIVALENT PRIVACY 64-bit or 128-bit protection ... Section 4 - Network Security & Advanced Device Techniques Created Date: 7/12/2017 2:55:38 PM ...
Types of Network Attacks and Prevention Techniques - Cyber ... Aug 01, 2019 · Last Updated on 8 months by Touhid. Network attackers are attempt to unauthorized access against private, corporate or governmental network infrastructure and compromise network security in order to destroy, modify or steal sensitive data. In this article, we will discuss on common types of network attacks and prevention techniques to protect …
What is advanced evasion technique (AET)? - Definition ... An advanced evasion technique (AET) is a type of network attack that combines several different known evasion methods to create a new technique that's delivered over several layers of the network simultaneously.
PDF Advanced Cyber Security Techniques - CEMCA Title Advanced Cyber Security Techniques Advisors Mr. R. Thyagarajan, Head, Admn. & Finance and Acting Director, CEMCA Dr. Manas Ranjan Panigrahi, Program Officer (Education), CEMCA Prof. Durgesh Pant, Director-SCS&IT, UOU Editor Mr. Manish Koranga, Senior Consultant, Wipro Technologies, Bangalore Authors
PDF Symantec Advanced Threat Protection: Network Symantec Advanced Threat Protection Symantec Advanced Threat Protection: Network is a solution that detects malicious content within a network by utilizing its Cynic malware detonation and global intelligence, its Vantage network intrusion detection, and its Insight reputation-based security technology to signal unknown and active threats.
GravityZone Advanced Business Security - Bitdefender GravityZone Advanced Business Security, is a next generation antivirus for businesses, built on the industry’s best prevention, detection and blocking capabilities. It uses machine learning, advanced heuristics, advanced anti-exploit technologies and other proprietary techniques to protect your endpoints and Exchange mailboxes.
Advanced Persistent Threat Protection: 7 Ways to Prevent ... Advanced persistent threats are malicious, secretive, and hard to detect. If you want to keep your data safe, then you need to know how to protect against APT attacks. 7 Best Practices for Advanced Persistent Threat Protection. Here's the hard truth about advanced persistent threat protection: No single solution will 100% protect you.
AV-Comparatives tested 15 Advanced Threat Protection IT ... In the Advanced Threat Protection Tests, AV-Comparatives use hacking and penetration techniques that allow attackers to access internal computer systems. These attacks can be broken down into ...
Sophos Email: Advanced Phishing & Cloud Email Security The same technology as our award-winning Intercept X, Sophos Email sandboxing is a deep learning neural network, able to block zero-day malware and unwanted applications. Stop Ransomware. The most advanced anti-ransomware technology available. Sophos email security uses behavioral analysis to stop never-before-seen ransomware and boot-record ...
Security Techniques for the Electronic Health Records Jul 21, 2017 · The most frequently mentioned security measures and techniques are categorized into three themes: administrative, physical, and technical safeguards. The sensitive nature of the information contained within electronic health records has prompted the need for advanced security techniques that are able to put these worries at ease.
Advanced Approaches to ATM Network Protection An Advanced Approach to ATM Security Security specialists who choose an advanced protection strategy should address all threat types using a security information and event management (SIEM)...
Malware Prevention: A Multi-Layered Approach - Cynet NGAV can detect and prevent malware that does not match a known binary signature, as well as fileless attacks that execute in memory or via network protocols without downloading a file to the target device. Control Privileges Control privileges on endpoints, servers, even administrator accounts, using the least privilege principle.
Network Antivirus: Sophos Advanced Security with EDR, MDR The world's best network antivirus solution Sophos antivirus protection for networks is built to stop ransomware, viruses, and advanced malware attacks in their tracks. Combining the industry's leading malware detection with endpoint detection and response (EDR), Sophos will future-proof your organization against both new and old threats.
PDF IT-2710: Advanced Topics in Network Security Provides in-depth understanding of network security principles and the tools and configurations needed to secure a network. Credit Hour(s): 3 Lecture Hour(s): 2 Lab Hour(s): 2 Requisites Prerequisite and Corequisite ITNT-2370 Network Security Fundamentals. Outcomes Course Outcome(s): Apply knowledge of advanced network security principles to ...



















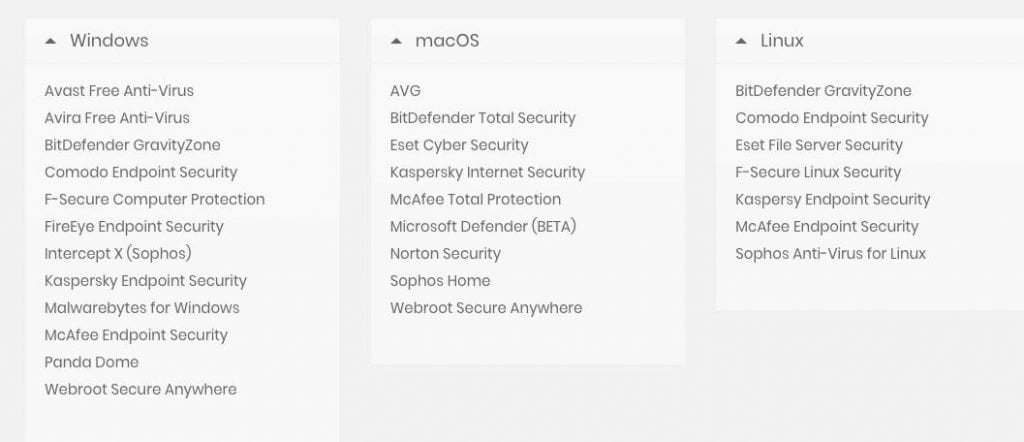




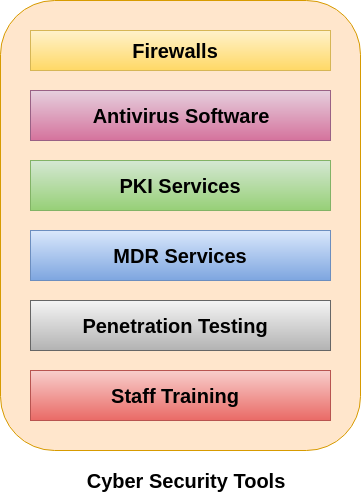



0 Response to "41 advanced antivirus techniques in network security"
Post a Comment