41 With Contemporary Antivirus Protection It Is Now Possible
10 Steps to Maximizing Your Antivirus Protection - iolo To get the most protection out of your antivirus, follow these ten best practices: 1. The most important step you can take is to keep the virus definitions for your antivirus current. Ideally, your antivirus automatically checks for updates, but if not, manually check once a day. 2. Do not install more than one antivirus. CrowdStrike Guide to Frictionless Zero Trust for Modern ... Observations from the front lines of Incident Response & Proactive Cybersecurity Services in 2019 - and key insights for 2020. Read Report. This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from ...
PDF MODERN PROTECTION AGAINST ATTACkS FROM THE INTERNET gurations should be possible in a centralized manner via the system. Higher security standards were called for in the e-mail system in Kiel too. The aim: to ensure greater protection against spam and malware such as viruses and Trojans. THE SOLUTION Thanks to a next generation firewall, the security system at the FH Kiel is now up to date.

With contemporary antivirus protection it is now possible
[Solved] With Contemporary Antivirus Protection It Is Now Possible ... With contemporary antivirus protection it is now possible to ensure a virus or malware never will attack your computer. Correct Answer: Explore answers and ...1 answer · Top answer: Answer of With contemporary antivirus protection it is now possible to ensure a virus or ... EOF Advances in Antiviral vaccine development Introduction. We are in a transitional time for antiviral vaccines. There are currently licensed vaccines that protect against 15 viral diseases (Table 1), but none have been licensed since the human papilloma virus (HPV) virus-like particle (VLP) in 2006.For the remaining emerging and re-emerging viruses for which vaccine development is a high public health priority, it may be necessary to ...
With contemporary antivirus protection it is now possible. Bus 230 Chapt 1 T/F Flashcards | Quizlet 5 Protecting Digital Intellectual Property: Means and ... Page 153. Technical Protection. The evolution of technology is challenging the status quo of IP management in many ways. This section and Appendix E focus on technical protection services (TPSs) that may be able to assist in controlling the distribution of digital intellectual property on the Internet. 1 The focus here is on how technical tools can assist in meeting the objectives stated ... Data Recovery Tips & Solutions: Windows, Linux, and BSD Kris Kaspersky · 2006 · ComputersIt is possible to leave the foo file; however, it might attract the attention of a vigilant user of an antivirus monitor. Now, it is time to explain the ... There is No Such Thing as True Privacy in the Digital Age (TNS) -- Nearly a week before WikiLeaks revealed that the Central Intelligence Agency may be using personal electronic devices for espionage, a lawsuit settlement admonished Facebook for reading...
Best antivirus software for 2022 - CNET A five-device subscription for Norton 360 with LifeLock Select is normally $99, but you can sign up for this virus protection software for $100 for the first year to get mobile security coverage... What is Information Security & Why is it Important? To make this possible, systems need to be updated and software backed up. "The careful implementation of information security controls is vital to protecting an organization's information assets as well as its reputation, legal position, personnel, and other tangible assets," the NIST said. Contemporary Business - Page 491 - Google Books Result Louis E. Boone, David L. Kurtz · 2011 · Business & EconomicsThis database now includes 4 million entries. ... Other Kaspersky antivirus utilities protect all of the 250 workstations worldwide, the 25 file servers, ... Beyond backup: Modern ransomware coercion tactics and how ... However, security teams should ensure they can recognize malicious intent, for instance if a device at the reception desk is conducting this activity, it will almost certainly be the result of a bad actor. At this stage, an attacker may also seek to identify which antivirus products are on the infected machine.
How to get a Windows memory dump - Micro Focus 31.05.2018 · Antivirus, anti-spam, anti-malware, and network protection. Secure Messaging Gateway (GWAVA) Protect your network and messaging system from malware, viruses, and harmful content . Voltage SecureMail . Scalable, end-to-end encrypted email solution for desktop, cloud, and mobile. Unified Endpoint Management › Unified Endpoint Management. Ensure all … ECIW2008- 7th European Conference on Information Warfare and ... Dr Dan Remenyi · 2008 · Computer securityHowever, because of the way contemporary forms of malicious software ... the annual expenditure on security systems that includes antivirus software. ReLoader Activator 6.6 With Crack 2022 Free Download [Updated] Download now. ReLoader Activator 6.6 Crack can be a light and reference-effective tool that does not necessarily take a great deal of your system’s running strength. It works several sizes. It is helpful for triggering the item of Microsoft Organization forever. Its one of the largest and the majority of extensive Ms activators, permitting users to allow or turn off all features of any ... Virus Bulletin :: Modern security software is not ... Still, it's possible that the authors of the malware made sure their latest creation bypassed those signatures too. Luckily, modern anti-virus often includes signature-less components, which blocks malware based on its behaviour. Now, a lot of malware tries to be as stealthy as possible to avoid behavioural detection.
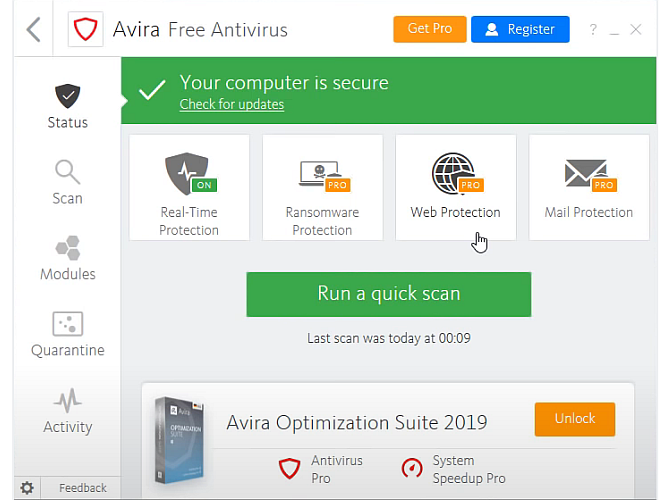
What is Antivirus Software? Download Free Antivirus ... - ESET That was mostly in the 1990s and in the beginning of the 2000s. However, with the dramatic growth in numbers of malware in other categories, antivirus programs have evolved into complex security solutions. To ensure their users' security, most contemporary protective products use multiple technologies.
Fix: VPN not working after Windows 10/11 update 01.03.2021 · In order to address this possible instigator of the problem with VPN, we’ll need to change the policy settings by inserting an exception for UDP. Now, the best way to do so is to use Registry Editor. Of course, with this tool we’re roaming in the dangerous area, so make sure to act with caution and don’t delete anything while there.
The rise of ransomware: How to protect a modern company The rise of ransomware: How to protect a modern company. In 2021, the cost of ransomware attacks is expected to exceed more than $20 billion worldwide. Ransomware has emerged as one of the most ...
Why Cyber Security is Important in The Modern Internet Age For example- The Melissa virus attack in the year 1999, the WannaCry ransomware attack in 2017, the NASA Cyber attack in 1999 etc. Councils like the National Institute of Standards and Technology (NIST) have begun releasing frameworks to help everyone understand the security risks, Cyber Security measures, and prevention methods.
(PDF) Computer Security and Mobile Security Challenges Computer security, also known as cybersecurity or IT security, is the protection of information systems from theft or damage to the hardware, the software, and to the information on them, as well...
Real-Time Programming 2004 - Page 80 - Google Books Result Matjaž Colnarič, Wolfgang A. Halang, Marek Węgrzyn · 2005 · Computerssome experts now recommend to update the installed " antivirus software ... that it is possible to build systems which can match the contemporary potential ...
Comodo IceDragon Browser | Download Free Internet Browser Comodo IceDragon is built over the core Firefox functionalities with enhanced privacy and protection features. For improved user experience, the browser also features Comodo Secure DNS, SiteInspector malware scanning and better social media integration. Is a 64-bit version of Comodo IceDragon available? As of now, the 64-bit version is not ...
AI-Powered Cybersecurity: From Automated Threat Detection ... Contemporary implementations include cloud-managed firewalls, real-time threat intelligence, and adaptive antivirus software that perform complex behavior analysis, thereby complementing traditional signature-based malware detection with advanced heuristics.
Exam 1 BCIS Flashcards - Quizlet Most e-book readers are usually smaller than smartphones. True With contemporary antivirus protection it is now possible to ensure a virus or malware never will attack your computer. Mobile Which of the following category of users works on a computer while away from a main office, home office, or school? Facebook
Contemporary Chief Information Officers: Management ... Hunter, M. Gordon · 2007 · Business & EconomicsIt is now necessary to justify costs associated with such aspects as software maintenance, network access, and annual maintenance fees.
COSC 1301 quiz ch.1 Flashcards | Quizlet With contemporary antivirus protection it is now possible to ensure a virus or malware never will attack your computer false looking for a keyboard to project from a device to a flat surface, which would you use virtual keyboard user that requires capabilities of a powerful computer power
How to Survive without Antivirus on Windows Computer ... Life without an antivirus seems unthinkable (atleast on Windows Computer). However, it is possible to live without antivirus. Without Antivirus installed, the need for a spending the resources of our computer no longer exists. And then the computer wins in speed and avoid major hassles, such as false alarms. Why live without antivirus?
Advances in Antiviral vaccine development Introduction. We are in a transitional time for antiviral vaccines. There are currently licensed vaccines that protect against 15 viral diseases (Table 1), but none have been licensed since the human papilloma virus (HPV) virus-like particle (VLP) in 2006.For the remaining emerging and re-emerging viruses for which vaccine development is a high public health priority, it may be necessary to ...
EOF
[Solved] With Contemporary Antivirus Protection It Is Now Possible ... With contemporary antivirus protection it is now possible to ensure a virus or malware never will attack your computer. Correct Answer: Explore answers and ...1 answer · Top answer: Answer of With contemporary antivirus protection it is now possible to ensure a virus or ...
/does-windows-10-need-antivirus-protection-4767578-1-7d4628e2729a47dea0a08e5cb2323cab.png)




/VPN-02.png?width=900&name=VPN-02.png)













![What to do when antivirus blocks VPN [4 tested solutions]](https://cdn.windowsreport.com/wp-content/uploads/2021/02/vpn.jpg)





/does-windows-10-need-antivirus-protection-4767578-1-7d4628e2729a47dea0a08e5cb2323cab.png)



0 Response to "41 With Contemporary Antivirus Protection It Is Now Possible"
Post a Comment